- Cybersecurity
- September 2, 2025
Table of Contents
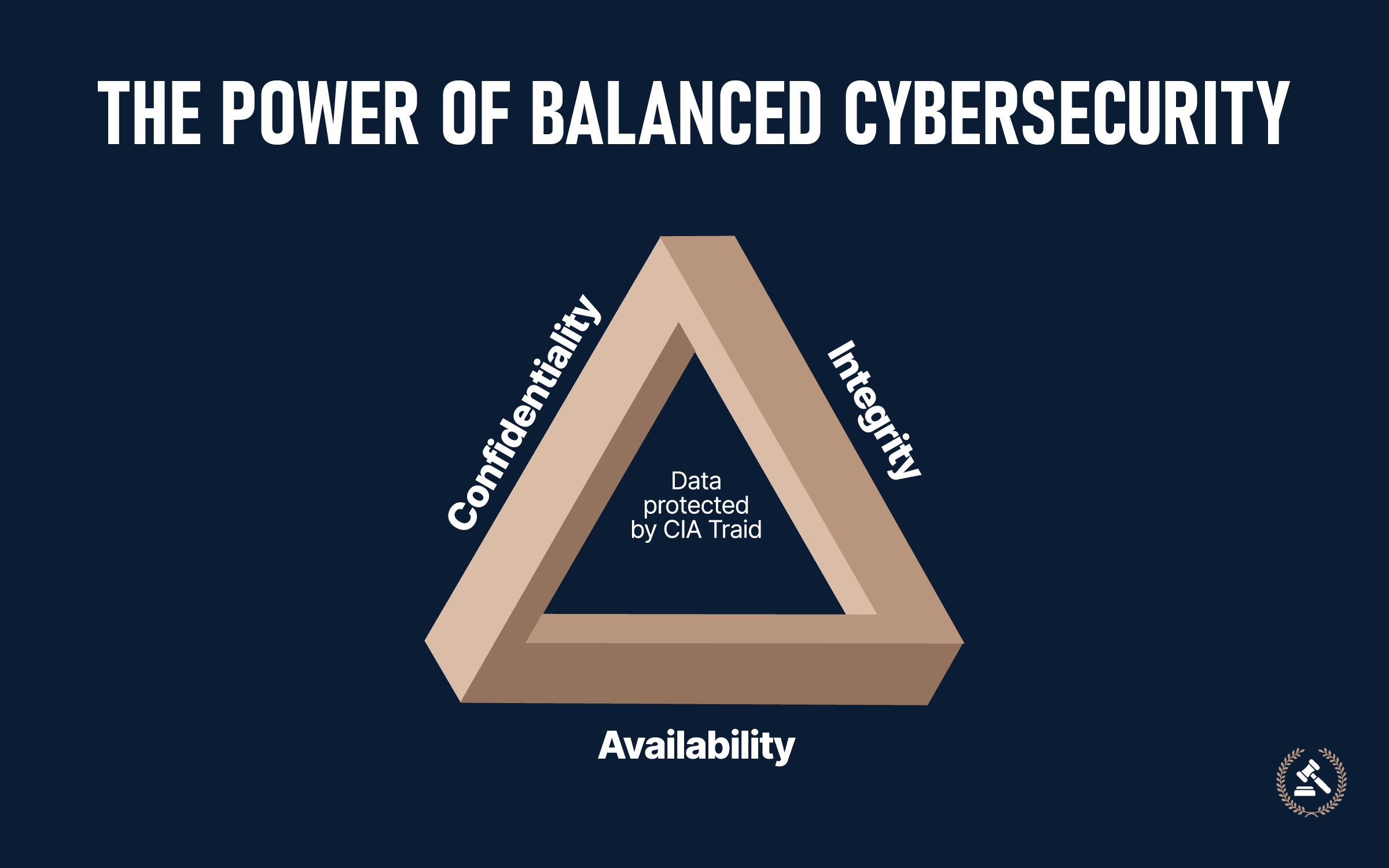
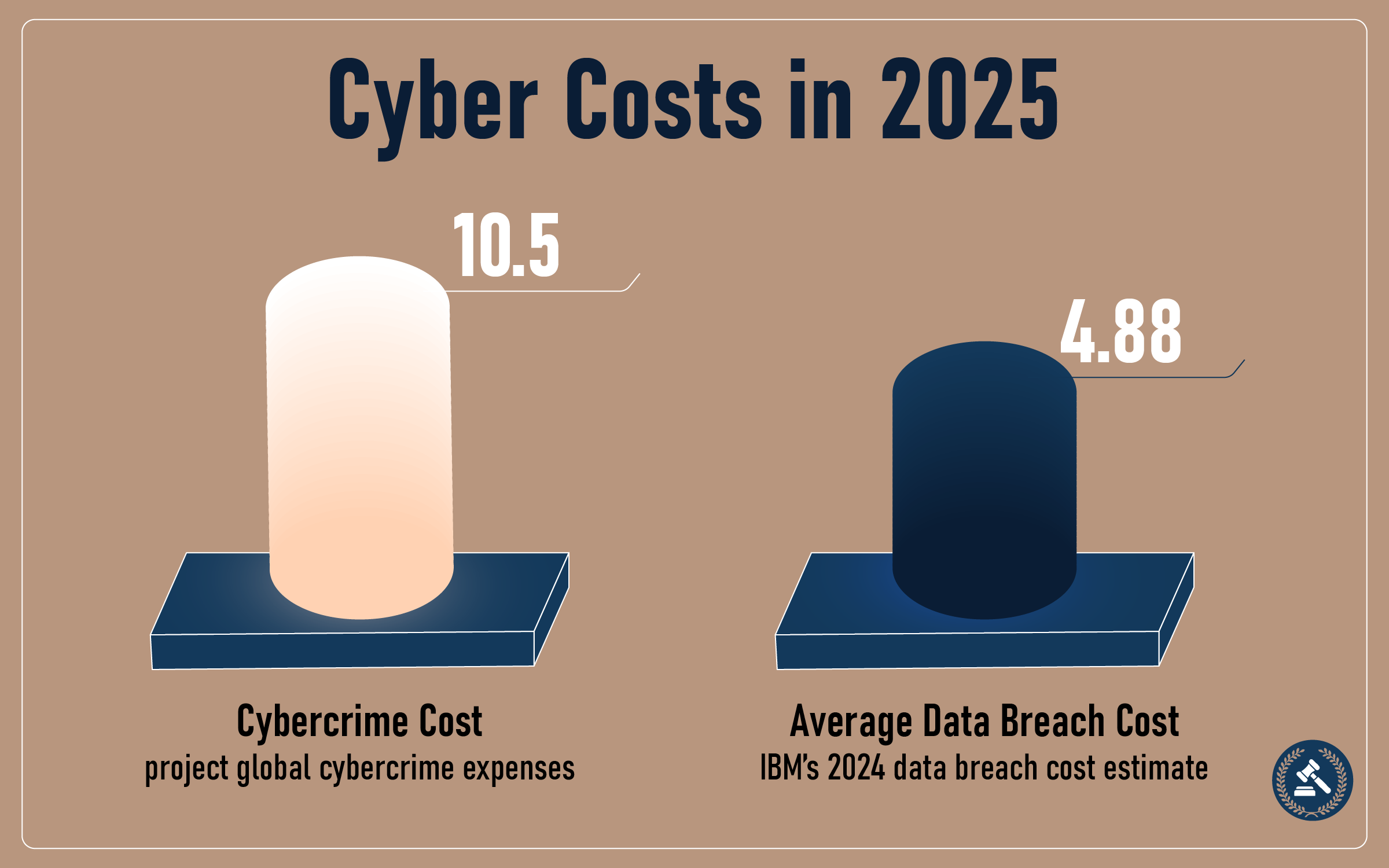
Three basic tenets of cybersecurity—Confidentiality, Integrity, and Availability (CIA Triad)—are the building blocks of digital security. As cybercrime is expected to cost $10.5 trillion in 2025 and the average data breach has cost $4.88 million in 2024, these principles are necessary to protect against sophisticated cyberattacks and reduce financial damage.
These terrible numbers again highlight the need for fundamental cybersecurity measures to protect the data, networks, and systems. At the core lies the security principle, structured by the CIA Triad: Confidentiality, Integrity, and Availability. Moreover, all security controls are decisions based on these three pillars:
- Confidentiality prevents unauthorized subjects from viewing or accessing sensitive information.
- Integrity preserves the accuracy and correctness of information.
- Availability ensures system and data access when required.
These three pillars should be understood and imbibed by any decision-maker or end-user, not only an IT professional. In securing an infrastructure for an enterprise or just guarding one's data, these principles give a solid construct toward security.
In the sections that follow, we’ll explore each tenet in depth—examining what they mean, why they matter, and how they help build a resilient, secure digital future.
Understanding the CIA Triad: The Foundation of Cybersecurity
The origins of the CIA Triad date back to the early periods of information security, and this framework evolved during the birth of computer networks and digital resources. It changed with time, hence becoming an accepted model of designing safe systems and policies as well as an architecture accepted within the world. Despite the changes brought on by the development of different technologies, including AI, cloud computing, and IoT, the CIA Triad remains as practical nowadays as it was in the past.
Although every tenet can exist separately in theory, they only function optimally as a cohesive system. For instance, integrity often necessitates collaboration between confidentiality and availability mechanisms. Vulnerability in one factor can degrade the others.
The CIA Triad is also used as a strategic compass for cyber protection teams. Access controls, backup policies, and intrusion detection are implemented with these three objectives in mind. It's not either-or; it's about balancing the correct amount in a situation and with regard to risk.
While some call it the AIC Triad (to distinguish it from the Central Intelligence Agency), the CIA name is still the most globally recognized term in the industry. Below are three principles that work together to create a complete security framework, starting with the foundation of keeping information secure.
First Tenet: Confidentiality
The confidentiality in cybersecurity refers to the safeguarding of information against unauthorized access or disclosure. It guarantees that sensitive information—personal, financial, or corporate—is only available to those specifically authorized.
Moreover, the "need-to-know" principle is the basis of confidentiality, and this involves limiting the access of data based on the role or purpose of its user. This would not only limit the exposed data but also most cases of insider threats.
Whereas usually linked to privacy, confidentiality has a wider context. Privacy is normally user-oriented, being concerned with personal data rights. Confidentiality, however, pertains to all sensitive data and is an important aspect of data protection principles in the public and private sectors.
Confidentiality Controls and Deployment
To ensure confidentiality, organizations employ layered security methods across network security, user access controls, and encryption.
Access Controls:
- Authentication: Passwords, biometrics, and multi-factor authentication authenticate the user.
- Authorization: Role-based access control (RBAC) controls access based on the role of the user.
- Permission Management: Systems apply policies to who can read, modify, or share data.
Encryption Technologies:
- Data Encryption: Secures data at rest and in transit.
- End-to-End Encryption: Only the sender and receiver can decrypt the content.
- Public Key Infrastructure (PKI): Facilitates secure communications and authentication.
Data Classification:
- Organizations classify data by sensitivity (e.g., public, confidential, restricted).
- A level of security is applied to each classification, enhancing efficiency and conformity.
Real-World Applications and Examples
Confidentiality is at the forefront in every business:
- Banking: Employs encrypted transactions and stringent access controls to protect financial information.
- Healthcare: Ensures confidentiality by utilizing HIPAA-compliant systems and electronic health record (EHR) safeguards.
- Corporate IT: Defends intellectual property, customer information, and trade secrets.
- Government: Classifies documents to control access to sensitive national information.
When confidentiality breaks down, breaches may result in data losses, financial losses, reputational losses, and regulatory fines. As one of the elements in the CIA Triad, it's an essential control for digital trust and security.
Second Tenet: Integrity
Within cybersecurity, integrity represents the guarantee that the data is truthful, complete, and not tampered with in any way at all times. It makes any information accessed by the users, whatever the given set of information, credible, as it has not been altered (unintentionally or intentionally).
The integrity of data should be differentiated from system integrity. Data integrity (e.g., the integrity of the content of a record of a transaction) does not imply system integrity (the platform that creates the information is running correctly).
In case of a breach of integrity, the results could be monetary misreporting of the companies, destruction of valuable data, damaged reputation, and poor decision-making.
Integrity Protection Methods
Organizations apply both procedural controls and technical safeguards to ensure integrity, as well as recovery systems through backup.
Technical Safeguards
- Checksums and Hash Functions: Assist in the detection of unauthorized alteration by comparing original and existing data.
- Digital Signatures and Certificates: Verify source and authenticate content integrity.
- Version Control Systems: Monitor file changes and avoid overwrites by mistake.
- File Integrity Monitoring (FIM): Follows up with administrators when important files are modified.
Procedural Controls
- Change Management: Assures updates go through documented approval procedures.
- Audit Trails: Log user activity for traceability.
- System Monitoring: Identifies abnormal behavior that may signify manipulation.
Backup and Recovery
- Redundancy Systems: Duplicate data to mitigate risk.
- Disaster Recovery Plans: Direct rapid recovery of correct data.
- Restoration Procedures: Ensure that recovered data retains its original integrity.
Integrity Challenges and Solutions
Data integrity is often compromised by:
- Malware modifies files or injects spurious data.
- Insider threats from employees altering records.
- Software bugs or crashes that destroy files.
To mitigate these threats, organizations ought to:
- Hash and verify important files periodically.
- Restrict write-access rights.
- Log monitor for evidence of tampering.
- Train employees in secure data habits.
Preserving data protection principles, such as integrity, is paramount in maintaining confidence in digital systems. Being one of the most important IT security definitions, integrity guarantees that your data isn't merely safeguarded but also reliable.
Third Tenet: Availability
Availability in cybersecurity refers to such systems and services as well as data that are open to users when they require them. The thing is to maintain an excellent uptime and minimize downtime.
Terms like "uptime," "downtime," and "Service Level Agreements" (SLAs) enable organizations to measure the performance and be able to state what is expected. Long delays would disrupt the business, corrupt the relationship with consumers, and cause economic damages—especially in the sectors of healthcare, finance, and online shopping.
Availability Assurance Strategies
Availability is backed by strong infrastructure, network security mechanisms, and regular maintenance.
Infrastructure Resilience:
- Redundant Systems: Duplicate hardware permits ongoing functioning upon failure.
- Load Balancing: Spreads traffic to prevent overloading any one server.
- Cloud Scalability: Enables systems to automatically scale at peak loads.
Threat Protection:
- DDoS Mitigation: Devices that identify and deny denial-of-service attacks.
- Firewalls & Intrusion Prevention Systems: Prevent unauthorized entry or overload attempts.
- Traffic Filtering: Prevents improper requests from reaching the system.
Maintenance and Monitoring
- Regular Updates & Patching: Remediate vulnerabilities that would lead to crashes.
- System Monitoring: Warns admins to possible performance problems.
- Performance Optimization: Improves response time and minimizes lag.
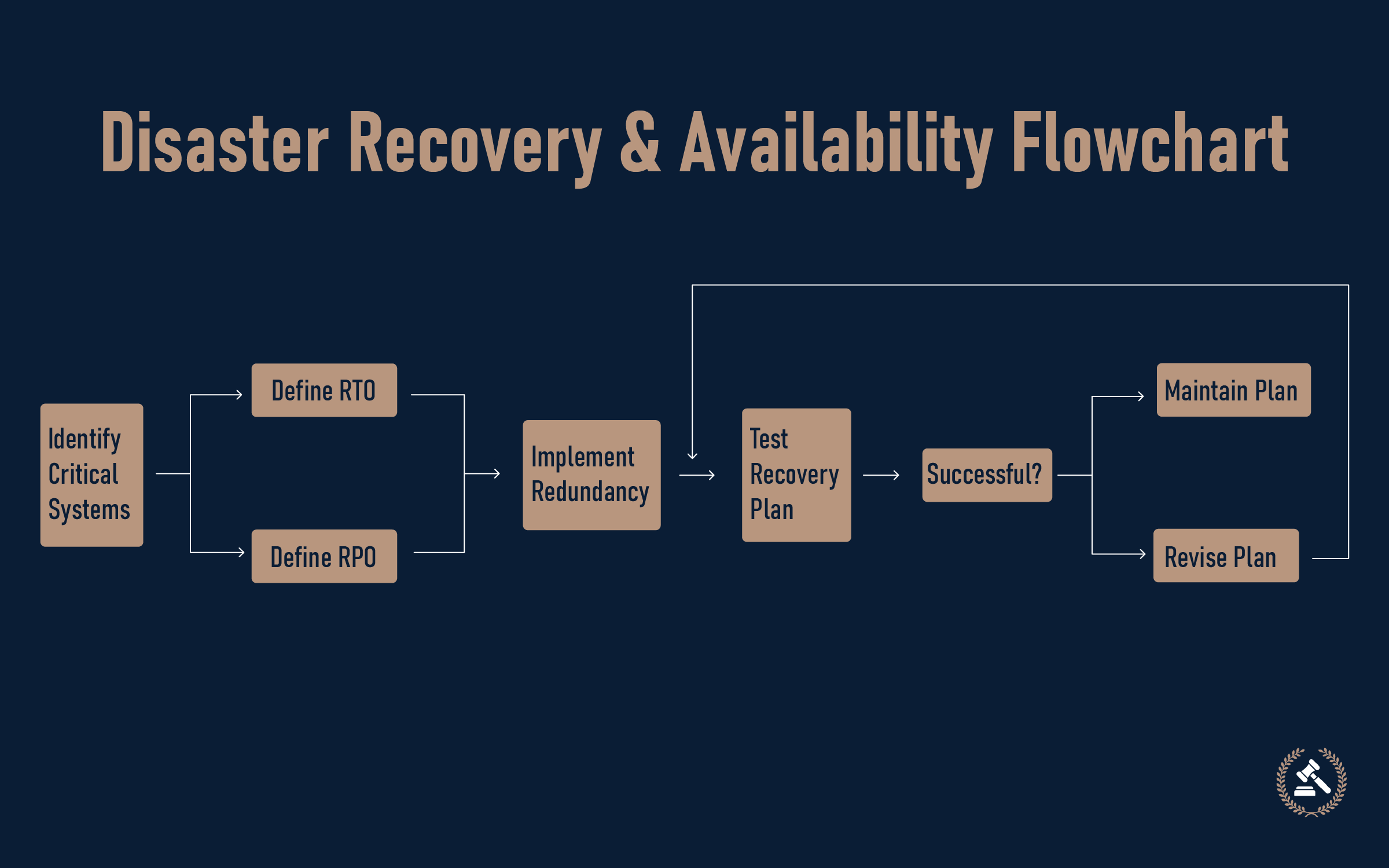
Disaster Recovery and Business Continuity
Despite robust defenses, downtime is at times unavoidable. That's where disaster recovery and business continuity planning are used.
The important practices are:
- Risk Assessment: Determines systems critical to operations.
- Recovery Objectives: Specify acceptable downtime (RTO) and data loss (RPO).
- Geographic Redundancy: Spreads data to several locations for failover protection.
Availability is the link between secure and usable data. Without it, even the most secure systems are useless. As a component of the CIA Triad, maintaining availability enables organizations to operate with confidence, even when they are under stress.
The Interconnected Nature of the CIA Triad
As the CIA Triad, Confidentiality, Integrity, and Availability, might seem distinct concepts, the concepts are, in real life, interconnected. These cybersecurity principles are the three pillars of cybersecurity that enhance the systems to be secure, dependable, and resilient.

The three principles can be used together in a complementary way. As an example, confidentiality can be delivered by encrypting information and therefore providing integrity by noticing changes that are not supposed to be made (integrity) or availability by simply using redundancy systems to support continuous access and agreeability on the quality of the data. There are, however, cases where there is interference between these goals, and such an organization must make compromises.
Scenario in life: A hospital emergency system considers availability such that it needs to be readily accessible at the expense of foregoing some of the controls of confidentiality. Confidentiality and integrity would matter to financial organizations, and they would agree to take longer to access their transactions to secure sensitive transactions.
The compromise is correct. The unfortunate side effect of overemphasizing one pillar is that this leads to the weakening of the others. Quality security design consequently looks at every component with specific threats, use case, and compliance requirements in mind.
The existing cybersecurity frameworks, CIA Triad, are used in existing cybersecurity homes like NIST and ISO/IEC 27001. They provide structured techniques of associating triads with emergent threats, business aims, and technology base.
Finally, triumph in cybersecurity is more than utilizing every single one of the tenets individually; it necessitates the complete, full-scale alignment of the three principles in your environment.
Know More About CIA Triad
Space and the CIA Triad are basic concepts of cybersecurity: Space, with availability, integrity, and confidentiality, is one of the pillars of basic cybersecurity concepts. All three fundamental principles help any safe system aim to make data privacy reliable and accessible.
And the three principles are all good, even in this threatening environment that is changing day in and day out. Cyberattacks can be modified, but the core element of any effective security plan is to make sure that the data is not accessed, manipulated against its will, and cut out.
Just like it is the case with risks, there is no assurance about cybersecurity in the absence of keeping it in mind; it suffices to implement steps to avoid it practically. Have access controls, encrypt or protect sensitive data, make integrity checks, and incorporate resiliency in the infrastructure.
As a business leader, an IT professional, or a regular user, the moment is the best time to review your cybersecurity stance. Have you ever thought of whether equal attention is also paid to all three pillars of the CIA Triad? What are the loopholes?
In the years to come, with the ongoing transformation of digital space by such big-hitter technological applications and platforms as AI, edge computing, and quantum-based encryption, we will have the CIA Triad on top of our common item list and agenda of adaptation and protection.
Cybersecurity is not a picture; it is a continuous responsibility. Start with the basics. Consolidate your base. Protect your own future.
FAQs (Frequently Asked Questions)
They are Confidentiality, Integrity, and Availability. Together, they function to give assurance that information is kept safe, is reliable, and is available when it is required. This model can be applied to nearly every cybersecurity technology and methodology.
Using end-to-end encryption in messaging apps or role-based access controls in enterprise systems ensures that only the specified users can access confidential information, ensuring confidentiality.
Data integrity ensures that data is not corrupted or modified. Hashing, audit logs, and digital signatures provide consistency and assurance of data.
If confidentiality is lost, data is exposed. If integrity is lost, the data is incorrect or damaged. Loss of availability means systems or data cannot be reached—each one creates significant security threats.
Cloud providers practice encryption for confidentiality, replication and backups for integrity, and redundant infrastructure for availability. Most also use compliance frameworks compatible with CIA tenets.