
- Cybersecurity
- August 21, 2025
Table of Contents
- What is 2FA and Why Does It Matter?
- How Does 2FA Help in Preventing Cybercrimes?
- Understanding Current Cyber Threats
- How 2FA Works?
- Types of Two-Factor Authentication (2FA): A Simple Guide for Everyday Users
- Why Passwords Alone Are Not Enough And How 2FA Fills the Gap?
- Limitations of Two-Factor Authentication (2FA)
- 2FA vs MFA: What is the Difference?
- 2FA Is Simple, Smart, and Totally Worth It
It often begins with a single alert like “Unusual login attempt detected.” Originally, it may seem like an innocent warning. But to others, that message is the start of something a lot worse: a hijacked account, an identity stolen, or an emptied wallet.
In today's digitally linked world, your banking and work applications, social apps, and cloud storage are all linked to your digital identity. And one compromised, reused, or stolen password opens the door to cybercriminals.
With high-profile data breaches and phishing attacks making headlines virtually every week, it's obvious that passwords are no longer sufficient. Even the most secure password can be hacked, guessed, or purchased on the dark web. Consider your password as the key to your home, but what if someone makes a copy of it without your notice?
This is where Two-Factor Authentication (2FA) helps. 2FA provides an additional layer of security to your password. It's an easy but effective way of securing your system, so even if someone with wrong intentions gets their hands on your password, your information remains secure, as they don't know about the second layer of your security system.
In this blog, we will describe 2FA, how it works, and why it is one of the smartest (and simplest) things you can do to enhance your security, whether you're safeguarding sensitive business infrastructure or your regular online logins.
What is 2FA and Why Does It Matter?
Let's consider a simple example: you close your house by locking it with a key while you are going to work. Similarly, in the world of the internet, this key is your account password. Suppose someone copied your key without your knowledge. You went out thinking that it was well locked, and this copied key holder can enter your house directly. That's frightful, isn't it?
Now picture this: on your door, you have installed a fingerprint reader with a lock and key. Even if someone were to get your key, they couldn't possibly get into your house unless they had the same fingerprint. Therefore, securing your house with additional security.
This is what 2FA is.
It's short for two-factor authentication. It puts an additional lock on your online accounts, an additional step to show you're actually you, and an additional layer of security for your logins. Rather than only entering a password (which, let's be honest, most people use again), 2FA requires something else that only you would have, such as a one-time code sent to your phone or a fingerprint.
So even if someone does take your password, they can't get in… because they don't have your second factor.
Definition:
Two-factor authentication (2FA) is an identity and access management security method that requires two forms of identification to access resources and data. 2FA gives businesses the ability to monitor and help safeguard their most vulnerable information and networks. - Microsoft.
Let us first understand what cybersecurity and cybercrime are before learning more about 2FA.
Cybercrime and cybersecurity, two sophisticated terms, but their definitions are straightforward.
Cybercrime is when someone uses the internet to steal, deceive, or cause harm. It could be a scammer sending fake emails that look like they're from your bank. It could be someone hacking into a company’s database to steal customer information. Or it could be a fraudster posing as a friend or family member, asking for money or personal details.
Anyone is a potential victim: a teenager who clicks on a link in an online game chat, a retiree logging onto their pension account, a remote worker, or the CEO of a large corporation
These are not unusual, distant tales; they are occurring daily, worldwide. As more of our lives become intertwined online, the threat is escalating.
Cybersecurity is all we do to safeguard ourselves from that. It's not exclusively a tech team's responsibility anymore. It's our job and your job.
That's why 2FA has become so popular. That's where 2FA saves the day.
How Does 2FA Help in Preventing Cybercrimes?
Let us revisit that message, "new login request from another device; enter your verification code to continue." Since you did not request this login, you can just click 'deny' on your phone and continue with your life.
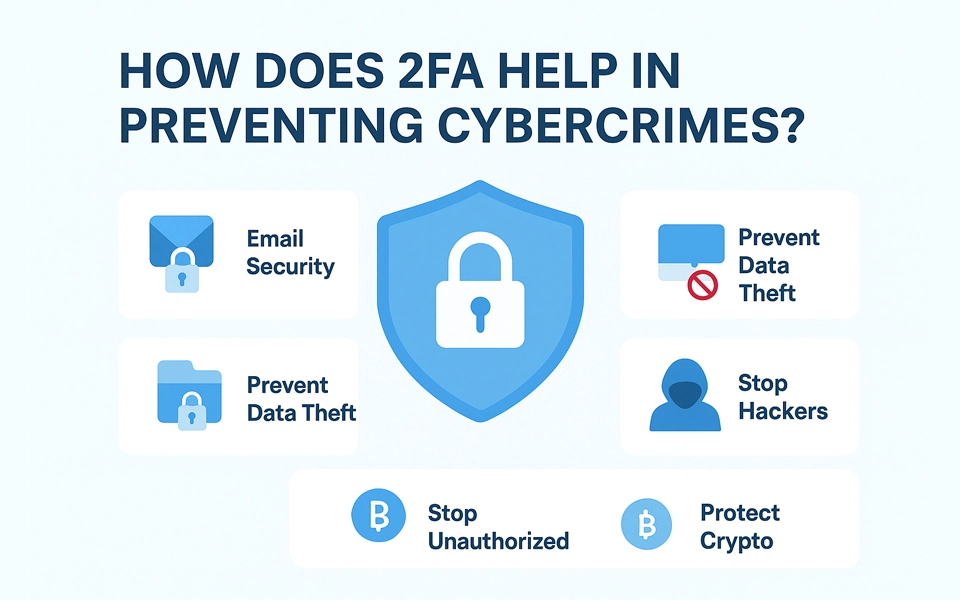
This 2nd factor verification code just secured your account. That individual had your password, possibly due to a data breach or because you reused your login, but not your second factor, because it is something uniquely yours. And without the second factor, there is no entry into your account.
2FA (Two-Factor Authentication) gives you that added security, something uniquely yours, such as your phone or biometric login.
- It's working behind the scenes to prevent:
- Unauthorized access to your email
- Unwanted purchases from your accounts
- Hackers from posting on your social media
- Data leaks at work or in your cloud storage
- Crypto wallet hijacks
Understanding Current Cyber Threats
The internet is an amazing tool, but just like anything powerful, it comes with risks. Don’t worry, we’re here to walk you through what’s happening out there and how you can stay one step ahead.
- Phishing has evolved. It has come a long way from just spam emails. Scammers can copy real messages or calls that have the voice of someone you know.
Tip: Pause before clicking or sharing, a second glance, a minute's pause goes a long way. - Credential stuffing? Sounds fancy, but here’s the idea: If you use the same password in multiple places, one leak can unlock more than you think.
Tip: Unique passwords (and a password manager) can stop that in its tracks. - Data breaches happen. When that happens, your stored information (like email, passwords, phone numbers, or even ID proofs) can be leaked or sold on the dark web. That exposed data can then be used by scammers to access your other accounts, and that doesn’t mean you’ve done anything wrong.
Tip: You can check if your info has been exposed and take action fast.
Today’s hackers use tools, not guesses. They automate and test vulnerabilities at scale.
This is where tools like 2FA and smart habits will make all the difference.
Cybersecurity isn’t about fear; it’s about confidence.With the right awareness and simple steps, you can protect yourself and feel more secure every day online. These days, banks, security experts, and even the FBI have recommended implementing 2FA in your systems.
How 2FA Works?
At its fundamental level, 2FA is based on a very simple yet potent structure: two levels of identity authentication. Rather than relying on a single credential (typically a password), it requests two distinct verifications to establish identity. This two-step approach renders it exceedingly difficult for cybercriminals to breach, even if the first layer is compromised.
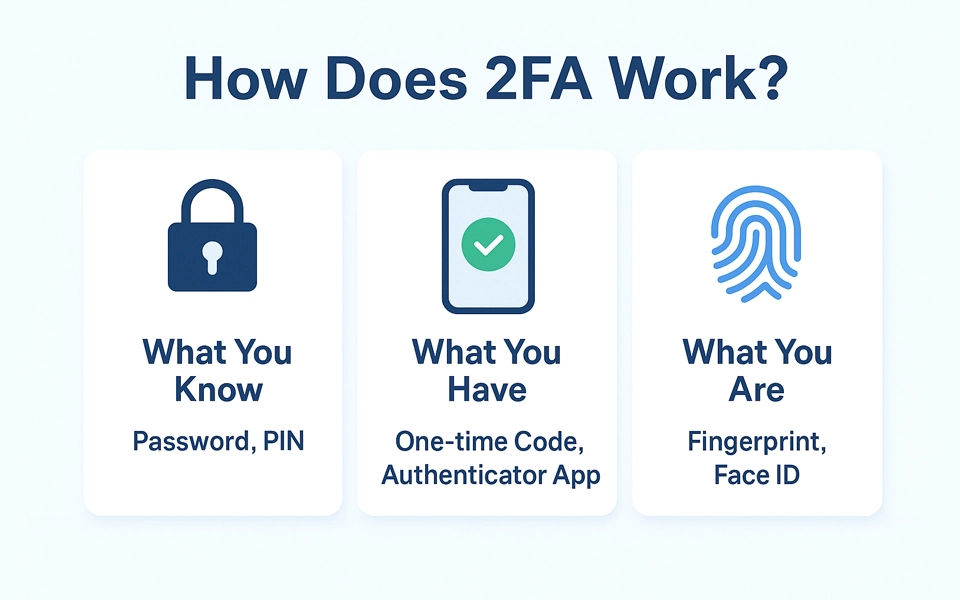
Layer One: Something That Only the User Knows
The first layer is familiar: a password, a PIN, or a pattern. It's something that the intended user should know by heart. This serves as the first gatekeeper.
But passwords alone are no longer sufficient. With phishing attacks, password compromises, and advanced hacking software on the rise, trusting solely in this first step leaves half a door open for hackers
Layer Two: Something the User Possesses
The second level is where the magic happens. It needs something that the user physically owns or is otherwise uniquely a part of. This may be:
- A one-time code cell phone
- An authenticator app that generates a time-based password
- A hardware token, which is plugged into a device
- Or even biometric data, like a fingerprint or facial scan
This second step is a confirmation that entry is not just being requested by a user who has the password; it's from an individual who also has the correct tool or is the appropriate individual.
Both of these layers, the mental one and the physical one, cooperate to create a secure checkpoint system. When one is compromised, the other keeps watch. That is why 2FA can prove so strong: it is not solely dependent on what an individual knows, but also on what they have or on who they are.
Today, with rising cyber threats, 2FA gives your password the extra support it needs. It's not just a better option; it's a simple, smart step that really fortifies your online protection
Types of Two-Factor Authentication (2FA): A Simple Guide for Everyday Users
Think of logging into your account like checking into a hotel. You give them your name and reservation number; that’s your password. But before they hand over the key, they ask for your ID. That extra step? That’s two-factor authentication (2FA). It’s a way of making sure you are really you.
-a-simple-guide-for-everyday-users.webp)
2FA adds a second layer of security beyond just a password. So even if someone knows your login details, they can’t get in without passing the second check. And depending on the platform, this second step can take different forms—from codes to apps to your fingerprint.
Let’s walk through the most common types of 2FA you’ll come across—and figure out which ones make the most sense for you.
1. SMS Verification (One-Time Code through Text Message)
When you log in with your password, a special code—a One-Time Password (OTP)—is sent to your phone by SMS. It typically expires in a few minutes, so it can't be reused. Minimal security on accounts such as email or social media. While simple to use, SMS can be intercepted via SIM swapping or phishing. Not good for high-risk accounts such as banking or cryptocurrencies.
2. Authenticator Apps
Apps such as Google Authenticator, Authy, and Microsoft Authenticator create time-based codes on your phone. These apps don't require internet connectivity and are safer than SMS because the code is generated locally on your device. What do people like about it? No waiting for a text message, and no chance that somebody could intercept the code, and you can connect multiple accounts and save them in case you change devices.
3. Push Notification Approval
Instead of entering a code, you get a prompt on your phone asking if you’re trying to log in. Just tap “Yes” to continue or “No” to block the attempt. It is super convenient, as there is no code, no typing, just one tap. This is popular with services like Duo, Microsoft, Google, and many financial apps.
4. Physical Security Keys
These are small hardware devices, like USB sticks, Bluetooth fobs, or NFC keys, that connect to your computer or phone during login. You’ll need to plug it in or tap it to approve access. Now this one is a top-notch protection, often used in industries where data security is non-negotiable. Developers, sysadmins, journalists, or anyone at risk of targeted attacks.
5. Biometric Authentication
Here’s where things get personal, literally. This method uses physical traits like your fingerprint, face, or iris to confirm who you are. The most common examples you must have seen are Face ID on smartphones and fingerprint scanners on your laptops. This one is gaining popularity at an increasing pace; it’s fast, secure, and already built into most modern devices. No code. No password. You just have to be you, and you can have access to your account.
Matching the Right Method to the Right Need
There is no one type of 2FA that suits all. What is most suitable usually depends on the risk, the hardware used, and the individual's technical comfort. For everyday use, authenticator apps or push messages are a good compromise between convenience and protection. For extremely sensitive accounts, hardware tokens or biometric factors offer better security.
What is most important is making 2FA available wherever possible. Every added layer, regardless of type, significantly decreases the likelihood of a breach, making a normal login a much safer endeavor.
At the end of the day, 2FA is not so much about tech and so much about feeling secure. You don't have to be an IT expert to utilize it, it's integrated into the apps and services you're already using. You just have to turn it on. So, if you haven't turned on 2FA yet, begin with baby steps. Use an authenticator app or biometric sign-in on your phone. It's an easy step that can protect your personal and financial information from the wrong people.
Why Passwords Alone Are Not Enough And How 2FA Fills the Gap?
A password is similar to a secret word spoken into a door lock. Convenient, but easily heard. These days, when information travels quicker than ever before, one whispered word is not enough to secure your accounts.
The Drawbacks of Passwords: Though they have been around since the dawn of digital access, passwords are no longer as reliable as they once were. They can be cracked, reused on multiple platforms, or leaked in a breach. No matter how intricate, once broken, a password provides no secondary defense.
This is where most systems are wanting; one key is safeguarding everything from mail to banking information.
Two-Factor Authentication: A Second Line of Defense
Two-Factor Authentication (2FA) flips the equation on its head by adding another layer of identity confirmation. Once a password is entered, the user is also required to authenticate access with something they have, like a verification code texted to a smartphone, an authenticator app, or even a biometric reader like a fingerprint.
This two-step method has the advantage of making sure that entry is not only dependent on something one knows but also upon something one controls physically.
Why It Matters?
2FA offers a practical defense against modern cyber threats. It:
- Prevents unauthorized access even if passwords are leaked
- Protects against phishing, keylogging, and brute-force attacks
- Strengthens data security for individuals and businesses
- Aligns with global security best practices and compliance standards
In short, passwords alone are outdated. 2FA adds a second gate, and in most cases, that’s the one attackers can’t get through.
Limitations of Two-Factor Authentication (2FA)
Okay, so 2FA is superior to using a password alone. But like all things, it's not foolproof. Here are a few of the problems that go along with it:
.webp)
- SMS can be attacked: SIM-swapping and phishing schemes can trick carriers into porting your number to another phone, allowing hackers in on your codes.
- You can be cut off from your second factor: Misplace your phone or security key, and you're out. Recovery procedures are a nuisance (and sometimes impossible if not stored).
- Folks still get phished: Certain sophisticated phishing attacks currently request your 2FA code in real time so that if you enter it, the criminal is still able to slip in before it times out.
- Doesn't secure everything: 2FA secures login, but if the app or service itself is hacked (consider data breaches), your information can still be vulnerable.
- It's a couple of seconds added: Let's get real, it's a tiny delay. But in today's world of instant gratification, even that can be frustrating when you're logging in 20 times a day.
2FA vs MFA: What is the Difference?
Here’s a quick comparison to clear the air between Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA). People often mix the two up, understandably!
|
FEATURES |
2FA |
MFA |
|
Definition |
Uses two distinct authentication factors (e.g., password + code) |
Uses two or more factors (can include biometrics, physical keys, etc.) |
|
Purpose |
Adds an extra layer beyond the password |
Maximizes security by using multiple barriers |
|
Examples |
Password + SMS OTP, |
Password + Fingerprint + Hardware token |
|
Flexibility |
Limited to just two steps |
Can involve multiple steps, tailored to the sensitivity level |
|
User experience |
Simple and faster for everyday users |
Slightly more complex, often used in enterprise or high-security cases |
|
Security Level |
Good for general protection |
Better suited for high-risk environments |
All 2FA is a form of MFA, but not all MFA is limited to just two steps. If you’re dealing with sensitive information or work in a high-security field, MFA is the stronger bet.
2FA Is Simple, Smart, and Totally Worth It
Let's get real, cyber attacks are all around. But turning on Two-Factor Authentication (2FA) is one of the simplest methods to secure your accounts and rest better tonight.
It may take an additional second to sign in, but that little bit of effort can prevent a giant headache. Whether it is your email, banking application, or crypto wallet, 2FA provides an incredibly effective second line of defense that most hackers won't be able to circumvent.
So if a site has it, enable it.
Use an authenticator app instead of SMS when you are able.
And don't wait till it's too late.
Because your online life is not worth sacrificing.
FAQs (Frequently Asked Questions)
Yes, you definitely do. Even the strongest passwords can be stolen in data breaches or guessed through phishing. 2FA acts like a second lock on the door, so even if someone gets your password, they still can’t gain access without that extra proof it’s really you.
Authenticator apps (like Google Authenticator or Authy) and physical security keys (like YubiKey) are your best bets. They’re much harder to hack than SMS codes, which can be intercepted. Biometrics (like your fingerprint or face) are also solid, just make sure your device is secure.
2FA is a solid first step, but for highly sensitive accounts, more layers are always better. Consider multi-factor authentication (MFA), which can combine an app, a physical device, and biometrics. Bottom line is NEVER rely on a password alone for anything that holds money or personal info.
Not necessarily! Most platforms let you set up backup codes, recovery emails, or trusted devices. But here's the catch, you have to set those up in advance. So do your future self a favor and have a backup plan in place.
It’s rare, but not impossible. The most common trick? Phishing, you get fooled into handing over your code. So always stay cautious, double-check links, and never share your one-time code with anyone, no matter how legit they seem.